Our SSO Journey
Numerator's journey to unified SSO for our customer-facing applications.
Overview
Single sign-on is an authentication process that allows users to securely access multiple related applications or systems using just one set of credentials. Ideally, once SSO has been set up, employees or customers can sign on just once to gain access to all authorized apps, websites and data from an organization or a connected group of organizations. - PingIdentity
Numerator provides access to Consumer insights through multiple customer facing applications like Numerator Insights, Promotions Intel and TruView. We have many common users across these applications, including external users and internal users like our developers, product managers and consultants.
Before we had an SSO solution, users had to setup and remember different credentials for each of these applications.
So in early 2021 we started our SSO journey to provide a unified and secure sign-in experience to our users.
First Shot: AWS Cognito
AWS is our primary cloud provider and so AWS Cognito was our first choice SSO provider. It was cost effective and easy to get started.
The AWS Cognito solution was composed of the following elements:
- A common API that our applications used to search and manage users and to send custom email messages for sign-up and password reset. (This API is composed of about 20 AWS Lambda functions.)
- A user administration application that had a React front end and a FastAPI powered backend API.
The following is a list of the main challenges associated with our AWS Cognito solution:
- Lambda cold starts and login issues for early users.
- Development team had to divide time between core feature work and maintaining the SSO solution.
Second Shot: Okta
In early 2022 we decided to switch over to Okta, so that we have minimum or no SSO related applications, API or code to manage.
We had to ensure that users were not impacted by this migration and that the change was transparent to them.
User and Password Migration
For user migration, we exported the user information (name, email, and groups) as a CSV, and then imported that information into Okta using a Python script.
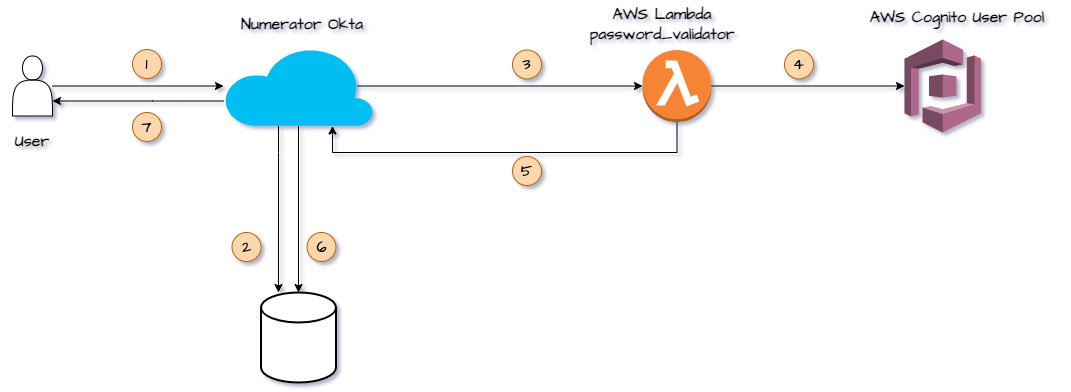
To migrate passwords we leveraged Okta's Password Import Hook feature, which works as follows:
- The User authenticates against Okta for the first time.
- Okta checks to see that the password has not been set.
- Web Hook sent to AWS Lambda as an API endpoint to validate the password.
- Password validated against AWS Cognito User Pool.
- Validation response sent back to Okta.
- If successful, Okta password is set.
- User successfully authenticated.
We left the password import hook on for three Months and most active users and their credentials were migrated, without them knowing or being disrupted in their usual workflow.
We used Okta's Users API to force password resets for the remaining users after three months, which prompted them to set new passwords via email.
SAML/OIDC Identity Provider Migration
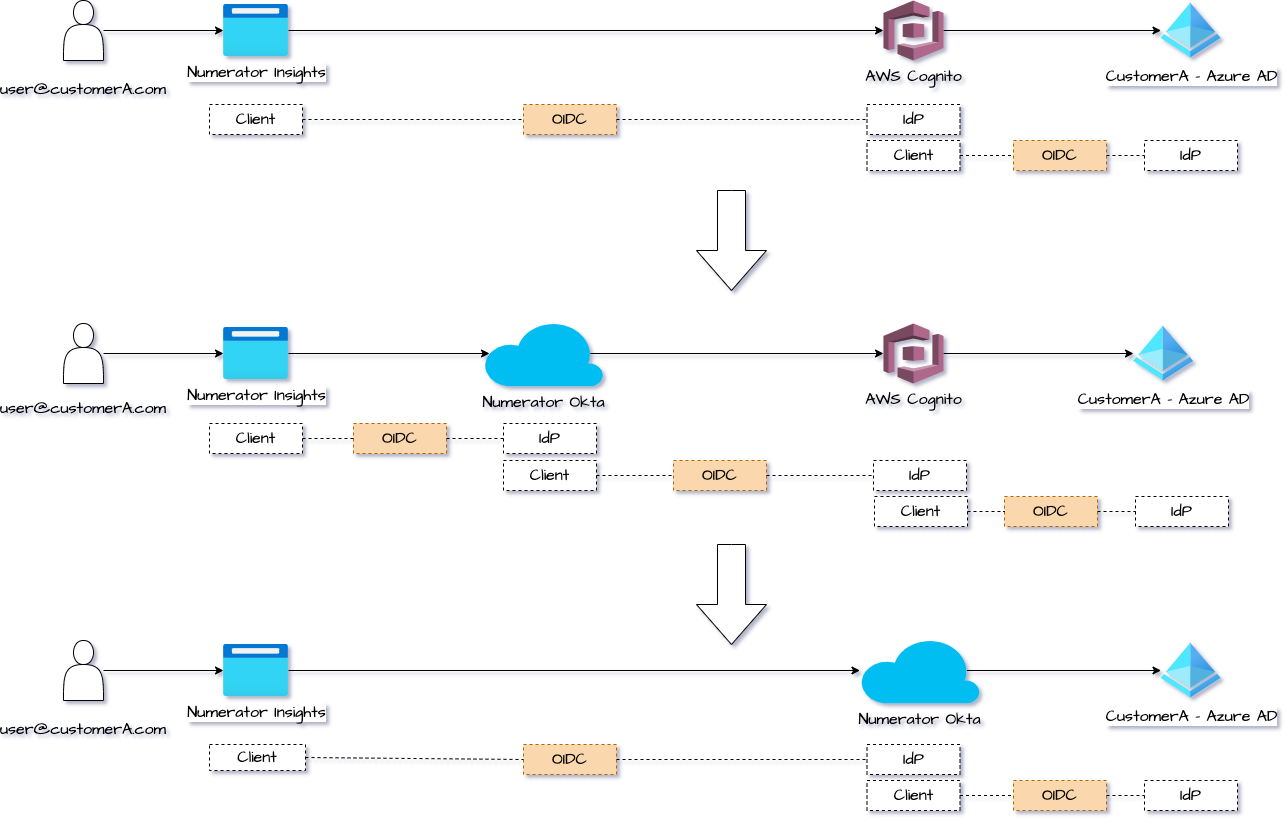
When we first migrated to AWS Cognito, we also federated logins for some our large customers to their organization-wide SSO provider. It allowed users to single sign-on using their organization credentials.
The Okta migration required that all customers create a new OIDC client for our Okta instance in their SSO provider. However, we did not want to delay the Okta launch until all customers had created a new OIDC client for Okta in their SSO provider. So we created an OIDC client and IdP relationship between our Okta and AWS Cognito instances which allowed us to migrate IdP for each customer at a different pace and not delay the launch.
User access based content in Numerator University
Numerator University is our learning platform. It hosts courses and videos that help our clients learn more about our products.
Numerator University is also secured using Okta SSO and additionally the content is filtered based on products that the user has access to. For example, if a user only has access to the Insights platform then all learning content related to Promotions Intel and TruView is hidden from the user.
Numerator University is a SaaS learning platform and content filtering can be enabled by assigning the right license to the learner. We enabled this by customising the OIDC tokens generated by Okta for Numerator University.
Conclusion
With Okta based SSO solution, Numerator was able to scale to more than 50,000 logins in a month for over 30,000 users across more than 10 apps.
Product teams now spend zero time troubleshooting login issues or running and maintaining user administration related application code. Instead, they can spend more time on feature work.
